The IT Buyer’s Guide to Managed IT Services: How to Choose the Right Partner
Finding managed IT services providers isn't hard, but finding the right one is. This guide helps you understand why you need a process to find good managed IT services companies and where you can find them.
Procuring IT services is one of the highest-risk decisions a technology leader makes. The market for managed IT services is highly saturated. Vendors frequently use identical marketing terminology, promise identical uptime guarantees, and claim to offer proactive support. Buyers often discover the reality of a vendor's capabilities only after signing a multi-year contract and handing over administrative access to their infrastructure.
Finding a reliable partner requires looking past the standard sales presentations. It requires understanding how vendors structure their pricing, how they monitor risk, and what happens when systems fail. This guide provides a systematic framework for evaluating, comparing, and selecting a managed IT services provider.
The Procurement Problem with Traditional IT Vendors
Comparing managed IT services is rarely a straightforward process. Buyers frequently receive three proposals from three different vendors, all containing completely different pricing structures and service definitions. This discrepancy makes objective comparison nearly impossible.
Evaluating Incompatible Pricing Models
Vendors construct their pricing models based on different operational philosophies. A 50-person organization might receive quotes ranging from $3,000 to $10,000 per month. The lowest quote often hides operational gaps.
Per-user pricing is the most common model in 2026. Providers charge a flat monthly fee for each employee, typically ranging from $100 to $250 per user depending on the service tier. This covers all devices associated with that user. It provides predictable monthly expenses and scales easily as the company grows.
Per-device pricing charges the business based on the exact number of workstations, servers, and network endpoints. Workstations might cost $50 to $100 each, while servers can cost up to $400 per month to manage. This model benefits companies with high headcount but low technology usage, such as manufacturing floors or retail environments.
Tiered pricing offers bundled services labeled as basic, standard, or premium. Buyers must scrutinize these tiers carefully. A basic tier might only cover remote monitoring and patch management. It often excludes onsite support or advanced security response, leading to unexpected hourly charges when complex issues arise.
Distinguishing Proactive IT from Break-Fix Support
Many vendors advertise proactive managed IT services but operate a reactive break-fix model behind the scenes. In a break-fix arrangement, the vendor waits for a system to fail before taking action. The client submits a ticket, the vendor fixes the issue, and the client pays an hourly rate for the labor.
True managed services operate on preventative maintenance. The provider actively monitors the network to identify failing hard drives, outdated firmware, or security anomalies before they cause downtime. They apply patches during off-hours. They conduct routine disaster recovery tests.
Buyers can test a vendor's proactive capabilities by asking for their preventative maintenance schedules. A reliable partner will produce documented workflows detailing exactly how and when they audit client environments. A vendor who cannot produce these documents relies heavily on reactive support.
Core Capabilities Required from a Managed IT Services Provider
Basic helpdesk support is no longer sufficient. Modern infrastructure requires a partner capable of securing endpoints, guiding technology strategy, and managing complex cloud deployments.
Advanced Cybersecurity and Compliance Standards
Security cannot be an add-on service. It must be integrated into the foundation of the managed IT services contract. Standard antivirus software and basic firewalls do not protect against modern ransomware or credential harvesting attacks.
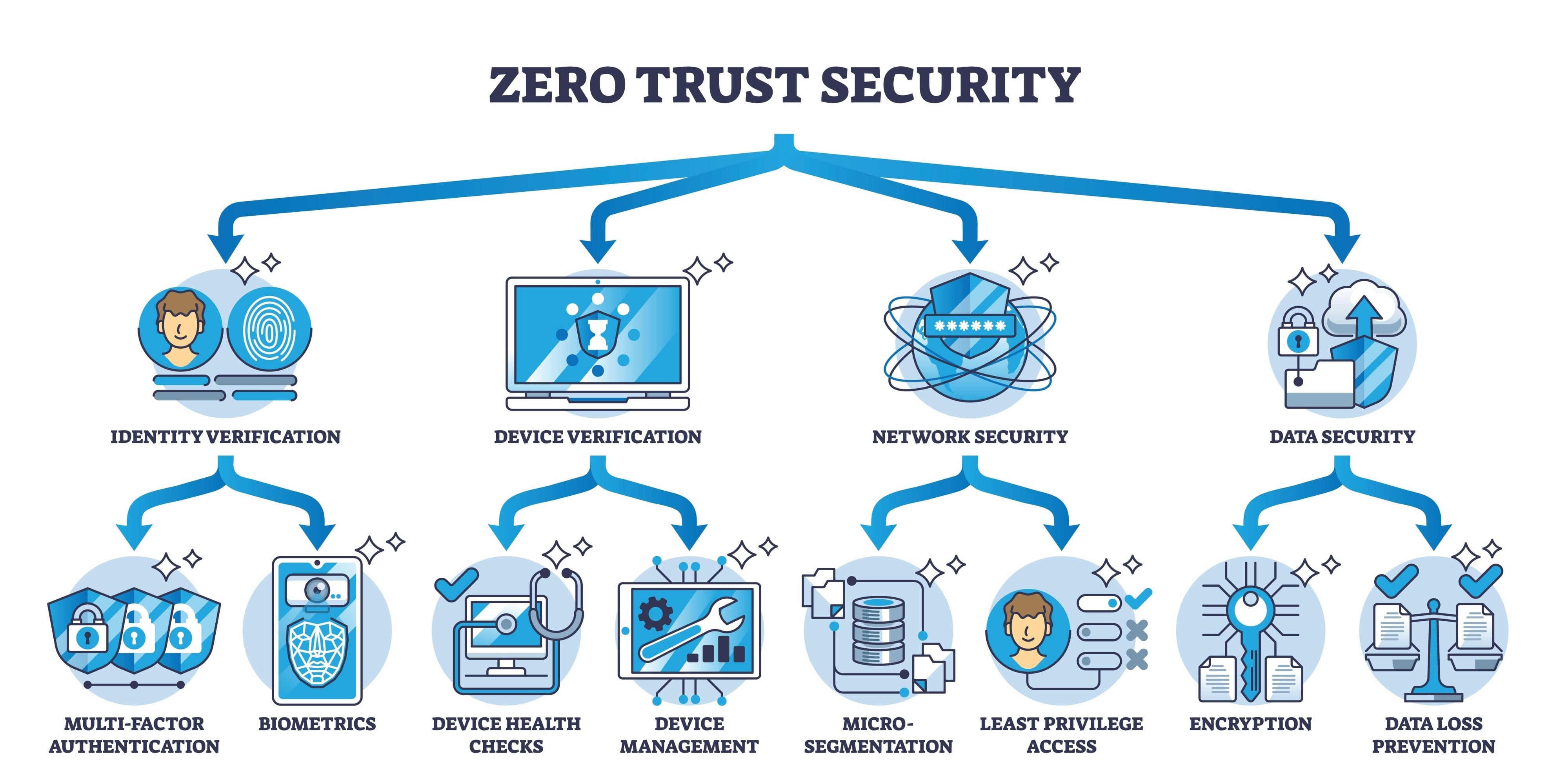
Vendors must deploy Endpoint Detection and Response tools. These tools monitor device behavior to stop malicious activity in real-time. They must also implement multi-factor authentication across all administrative access points.
Compliance is another critical factor. Organizations operating in healthcare, finance, or defense face strict regulatory requirements like HIPAA, SOC 2, or CMMC. The managed IT provider must have documented experience maintaining these compliance frameworks. They need to generate the audit logs and access reports required by regulatory bodies. If a vendor treats compliance as an afterthought, they expose the buyer to massive legal and financial liabilities.
Strategic IT Consulting and vCIO Services
A capable IT partner acts as a strategic advisor. This function is typically delivered through a Virtual Chief Information Officer. The vCIO bridges the gap between technical execution and business strategy.
The vCIO conducts quarterly business reviews to assess the current technology stack. They analyze ticket trends to identify recurring issues that require permanent solutions. They help build annual IT budgets, plan hardware refresh cycles, and evaluate new software investments.
Providers lacking vCIO capabilities limit their value to basic maintenance. They fix broken laptops but fail to guide the business through digital transformation or scalability challenges. Buyers should ask for a sample vCIO roadmap during the evaluation process to verify the vendor's strategic depth.
Cloud Infrastructure Management and Scalability
On-premise servers are increasingly rare. Most businesses operate in hybrid or fully cloud-based environments using Microsoft Azure, Amazon Web Services, or Google Cloud. The chosen IT partner must possess advanced certifications in these specific platforms.
Cloud management requires different skill sets than traditional server maintenance. Vendors must understand cloud cost optimization to prevent monthly hosting bills from spiraling out of control. They must secure cloud applications against unauthorized access and configure automated backups for cloud data.
Scalability is equally important. The vendor must demonstrate the capacity to support the business as it expands into new locations or hires remote workers across different time zones. A vendor that struggles to support a 50-person company will fail catastrophically when that company grows to 200 employees.
Disaster Recovery and Business Continuity Execution
A cyber attack or natural disaster will eventually disrupt operations. A competent managed IT services provider anticipates this reality. They build and regularly test strict Business Continuity and Disaster Recovery plans. They do not just back up data to a local hard drive. They replicate entire server environments to secure, geographically isolated data centers.
Buyers must ask vendors for their standard Recovery Time Objective (RTO) and Recovery Point Objective (RPO). RTO dictates exactly how fast systems come back online. RPO dictates how much data the business loses during the restoration process. If a vendor cannot commit to specific RTO and RPO metrics in writing, they cannot guarantee your operational survival.
Co-Managed IT and Internal Team Integration
Mid-market organizations frequently maintain a small internal IT team. They do not need a vendor to replace their staff. They need a managed IT services provider capable of executing a co-managed IT model. This arrangement supplements internal capabilities with specialized external resources.
The vendor must demonstrate exactly how they integrate with your existing workflows. They need to provision shared access to their IT Service Management platform. This shared access creates a unified ticketing system. It allows your internal staff to handle daily employee requests while instantly escalating complex infrastructure or security incidents to the vendor's Tier 3 engineering team.
The Buyer’s Checklist: Evaluating Vendor Contracts
The contract dictates the reality of the partnership. Sales promises mean nothing if they are not explicitly codified in the Master Services Agreement and the Service Level Agreement.
Defining the Service Level Agreement Guarantees
The Service Level Agreement defines the vendor's commitments regarding response times, resolution times, and system uptime. Buyers must read this document with extreme skepticism.
Many vendors guarantee a one-hour response time. Response time only measures how quickly the vendor acknowledges the ticket. It does not measure how quickly they actually fix the problem. A vendor can achieve a 100 percent success rate on response times simply by sending an automated email reply.
Buyers must insist on Mean Time to Resolve metrics. This metric defines the average time required to completely fix an issue and restore normal operations. The agreement must also include financial penalties if the vendor fails to meet these targets. If there is no financial consequence for poor performance, the Service Level Agreement is meaningless.
Furthermore, buyers should ask how the vendor tracks SLA risk. Many vendors only monitor compliance, meaning they only look at the data after an SLA is already breached. Mature providers monitor technician workload and ticket aging patterns to identify and resolve risks before a breach occurs.
Establishing a Secure Onboarding Process
The transition from an internal IT team or a previous vendor to a new provider is a highly vulnerable period. Poor onboarding leads to lost passwords, undocumented network configurations, and massive employee frustration.
A professional onboarding process takes 30 to 90 days. The new vendor must deploy discovery agents to map the network and identify all connected devices. They must audit existing security policies and document all software licenses. They need to establish secure remote access protocols and train the employees on how to submit support requests.
Buyers should demand a detailed, step-by-step onboarding project plan before signing the contract. If the vendor claims they can take over the network in a few days, they are bypassing critical security and documentation steps.
Securing Administrative Access and Data Ownership
Data hostage situations happen frequently in the IT industry. A business decides to terminate their contract with a poorly performing vendor. The vendor then refuses to hand over the global administrator passwords for the company's servers, domain names, or cloud hosting accounts.
The contract must explicitly state that the buyer retains sole ownership of all data, hardware, and administrative credentials. The buyer must hold a master copy of all passwords in a secure password manager that they control. The vendor is granted access to perform their duties, but the buyer can revoke that access at any time.
Additionally, the contract must include a clear offboarding clause. This clause mandates that the vendor will cooperate fully with any future IT providers during a transition period.
The Financial Impact of Poor Vendor Selection
Choosing the cheapest vendor often results in the highest total cost of ownership. Budget providers maintain low prices by overloading their technicians and utilizing offshore support desks with poor communication skills.
The hidden costs of a bad IT partnership compound quickly. When technicians are overloaded, tickets sit untouched for days. Employees cannot work, leading to thousands of dollars in lost productivity. Small network issues escalate into major outages because the vendor lacks the resources to monitor the systems proactively.
Security breaches are the most expensive consequence of poor vendor selection. Budget providers rarely invest in their own internal security. Hackers frequently target weak managed IT providers to gain access to all of their clients simultaneously. If the vendor fails to deploy adequate ransomware protections, the buyer faces catastrophic data loss, regulatory fines, and permanent reputational damage.
Investing in a premium managed IT services provider functions as an insurance policy. The higher monthly fee prevents the massive financial losses associated with downtime and cyber attacks.
Where to Find and Vet Reliable IT Managed Services
Finding a reliable partner requires looking beyond basic search engine results. Several platforms and methodologies exist to help buyers evaluate potential vendors objectively.
Traditional Review Platforms: Clutch, G2, and Trustpilot
B2B review platforms aggregate client feedback and operational data. Platforms like Clutch verify reviews by conducting phone interviews with the vendor's clients. This verification process filters out fake testimonials.
Buyers can use these platforms to filter vendors by hourly rate, industry focus, and minimum project size. G2, Capterra, and Trustpilot offer similar functionalities, focusing heavily on client satisfaction scores and market presence. While these platforms provide valuable preliminary data, they place the burden of deep technical vetting entirely on the buyer.
Research and Advisory Firms: Gartner and Forrester
Large enterprises frequently rely on advisory firms like Gartner and Forrester. These firms publish exhaustive research reports evaluating the technical capabilities of global managed service providers.
Their reports are highly objective and technically rigorous. However, they primarily focus on massive, enterprise-level vendors that require millions of dollars in annual spending. Small and mid-market buyers will find these reports informative but practically useless for finding a local or regional partner.
Vetted Matchmaking Marketplaces: TechnologyMatch
Modern procurement is shifting toward curated matchmaking marketplaces. Platforms like TechnologyMatch operate differently than static review sites. They actively pre-vet IT service providers before allowing them onto the platform.
This vetting process involves auditing the vendor's security practices, verifying their response time metrics, and checking their compliance certifications. Buyers submit their specific technical requirements, budget constraints, and industry regulations. The platform then matches the buyer with a curated shortlist of vendors who are uniquely qualified to execute the contract.
This model eliminates the need for buyers to conduct exhaustive background checks or decipher incompatible pricing models. It standardizes the evaluation process and significantly reduces the risk of selecting an incompetent provider.
Looking for IT partners?
Find your next IT partner on a curated marketplace of vetted vendors and save weeks of research. Your info stays anonymous until you choose to talk to them so you can avoid cold outreach. Always free to you.
FAQ
What is the average cost of managed IT services in 2026?
Pricing depends heavily on the chosen model and required security standards. On average, businesses can expect to pay between $100 and $250 per user per month. Complex environments with strict regulatory compliance requirements will push costs toward the higher end of that spectrum.
What is the difference between an MSP and an MSSP?
A Managed Service Provider handles general IT operations, helpdesk support, and basic security. A Managed Security Service Provider focuses exclusively on advanced cybersecurity, continuous threat monitoring, incident response, and complex compliance frameworks. Many modern vendors now blend these capabilities.
How do I safely transition to a new IT provider?
A safe transition requires a documented 30 to 90-day onboarding plan. Before terminating your current vendor, secure global administrative access to all critical systems. Allow the new vendor to deploy discovery tools to map the network and take control of the environment systematically.
Why do Service Level Agreements fail?
SLAs typically fail because they use vague language regarding the scope of services. They often measure response times instead of resolution times, giving the illusion of fast service while problems remain unfixed. They also frequently lack strict financial penalties for underperformance.
What is a vCIO and why do I need one?
A Virtual Chief Information Officer is a strategic advisor provided by the IT vendor. They align your technology infrastructure with your business goals. They manage IT budgets, plan hardware upgrades, and ensure your technology stack scales efficiently as your company grows.





