IT Vendor Evaluation for Compliance-Heavy Industries (HIPAA, SOC 2)
Risk-first IT vendor evaluation framework for healthcare, finance & SaaS. Includes SOC 2, HIPAA, vendor risk checklist & scoring model.

In most corporate environments, evaluating a new IT vendor is an exercise in feature comparison, pricing negotiations, and implementation speed. If the software has a clean user interface and fits the budget, the deal gets done.
In compliance-heavy industries, that approach will eventually cost you your job, your company’s reputation, and potentially millions in regulatory fines.
If you operate in healthcare, financial services, government contracting, or enterprise B2B SaaS, vendor failure is not an operational inconvenience. It is a compliance event. When a vendor suffers a data breach, violates data sovereignty laws, or fails a disaster recovery test, the regulatory body does not penalize the vendor. They penalize you. You cannot outsource your legal liability.
In these high-stakes environments, IT vendor evaluation must completely shift from a feature-first mindset to a risk-first methodology.
This guide provides a structured, operational playbook for evaluating enterprise IT vendors when your organization is subject to strict regulatory oversight. It is designed to help lean IT teams bypass marketing fluff, evaluate actual operational risk, and survive the grueling security audits that define modern enterprise procurement.
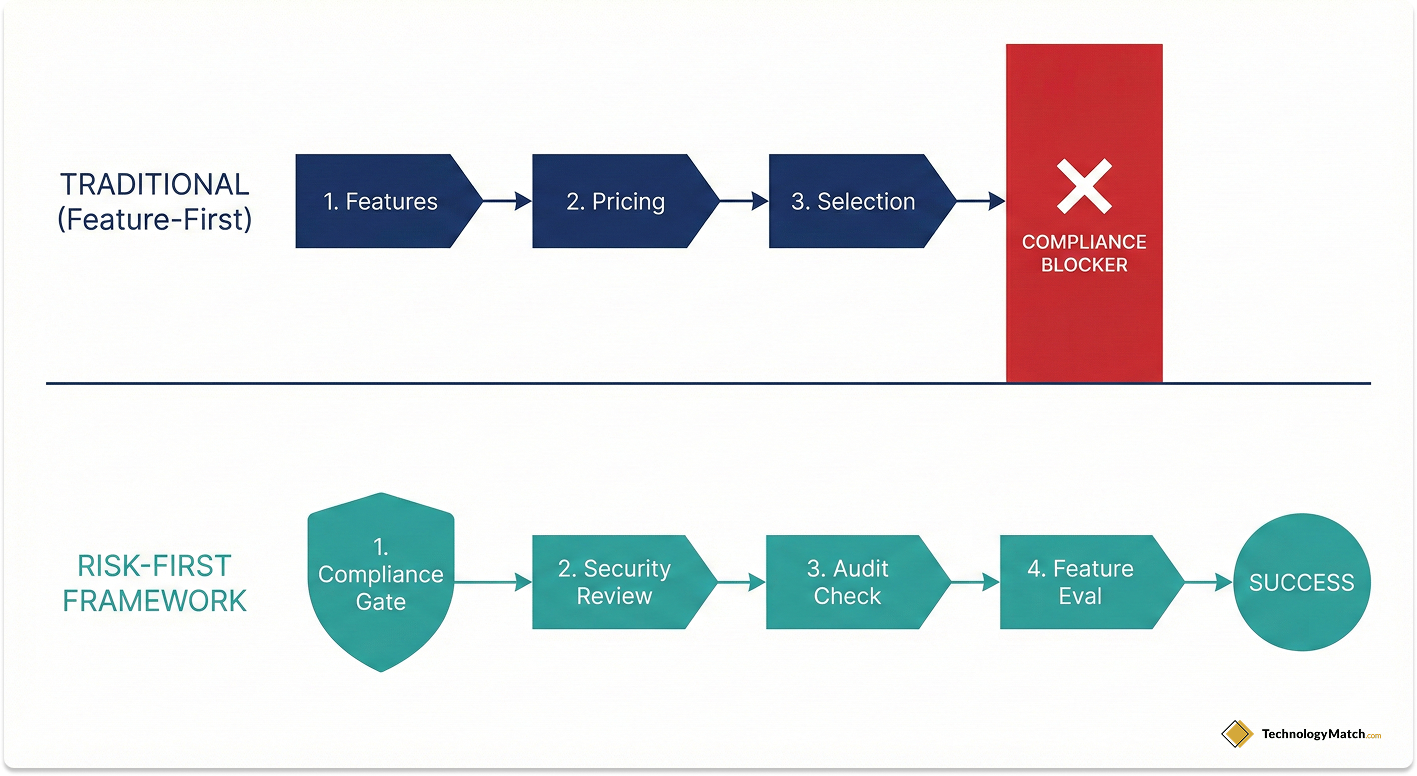
Why Compliance Completely Changes Vendor Evaluation
The traditional vendor selection process is fundamentally broken for regulated industries. Standard advice tells you to gather requirements, watch product demos, compare features, and then, at the very end of the process, hand the contract to your legal and security teams for a quick review.
When you follow this path in a compliance-heavy environment, you will routinely spend six to eight weeks falling in love with a software platform, only to have your compliance officer kill the deal on Day 60 because the vendor refuses to sign a Business Associate Agreement (BAA) or lacks a current SOC 2 Type II report.
This is a massive drain on your IT team's limited bandwidth.
To survive, you must flip the funnel. Compliance must become the absolute first filter, not the final checkbox.
The Core Definition
IT vendor evaluation in compliance-heavy industries is a risk-first assessment process that prioritizes regulatory alignment, audit readiness, and security transparency over feature comparison alone.
The order of operations matters. If a vendor cannot definitively prove they meet your regulatory baseline on Day 1, their feature superiority is entirely irrelevant. You must disqualify them immediately and move on.
What Makes an Industry “Compliance-Heavy”?
An industry transitions from "standard" to "compliance-heavy" when three things happen:
- Regulatory frameworks impose strict, legally binding data protection obligations.
- Your customers (or government entities) actively audit your internal systems and your supply chain.
- Third-party vendor risk directly impacts your own ability to maintain certifications.
Let’s break down the three primary environments where this risk-first framework is mandatory.
1. Healthcare (HIPAA, HITECH, Regional Health Data Laws)
Healthcare IT leaders are not just managing networks; they are the custodians of Protected Health Information (PHI). The regulatory scrutiny is unforgiving.
- The Business Associate Agreement (BAA): A vendor is legally barred from touching PHI unless they sign a BAA, which legally binds them to HIPAA standards. Many modern SaaS tools refuse to sign these.
- Encryption Standards: Data must be encrypted both in transit and at rest, ideally with the healthcare organization retaining control of the encryption keys.
- Breach Notification: HIPAA requires specific, rapid notification timelines in the event of a breach. Vendors must contractually guarantee they can meet these SLAs.
- The Stakes: Vendor failure in healthcare leads to OCR (Office for Civil Rights) investigations, massive civil penalties, and the catastrophic loss of patient trust.
2. Financial Services (SOX, PCI-DSS, FFIEC, GLBA)
Banks, credit unions, and fintech startups handle Personally Identifiable Information (PII) and highly sensitive financial data. Their vendors are actively targeted by state-sponsored threat actors.
- Immutable Audit Trails: Financial regulations require proof of exactly who touched what data and when. Vendors must provide logging that cannot be altered or deleted by internal administrators.
- Data Sovereignty: Financial data often cannot cross borders. Vendors must prove exactly which physical data centers will house the information.
- Continuity and Uptime: The FFIEC requires rigorous disaster recovery and business continuity planning. A vendor going offline cannot cause a bank's operations to halt.
- The Stakes: Vendor failures here result in SEC fines, PCI compliance revocation (meaning you can no longer process credit cards), and systemic financial risk.
3. Enterprise SaaS Providers (SOC 2, ISO 27001, GDPR)
You might build software for a living, but if you sell to enterprise clients (like Fortune 500s or hospitals), you inherit their compliance requirements.
- The Cascading Effect: To pass your own SOC 2 Type II audit and close enterprise deals, you must prove that all of your sub-processors (AWS, Datadog, Okta, Zendesk) are also compliant.
- Continuous Security Reviews: Your sales team cannot close deals unless your IT team can quickly answer 300-question security assessments from buyers.
- Data Portability and Deletion: To comply with GDPR's "Right to be Forgotten," your vendors must give you the tools to surgically delete specific user data across all backups and active databases.
- The Stakes: Vendor failure in enterprise SaaS directly kills your sales pipeline. If your hosting provider fails their SOC 2 audit, your enterprise customers will churn.
The 5-Layer Compliance Vendor Evaluation Framework
To evaluate vendors efficiently without relying on vendor marketing promises, you must use a structured, binary filtering system. This is the 5-Layer Compliance Vendor Evaluation Framework.
A vendor must pass Layer 1 to reach Layer 2. If they fail at any layer, they are disqualified from the procurement cycle.
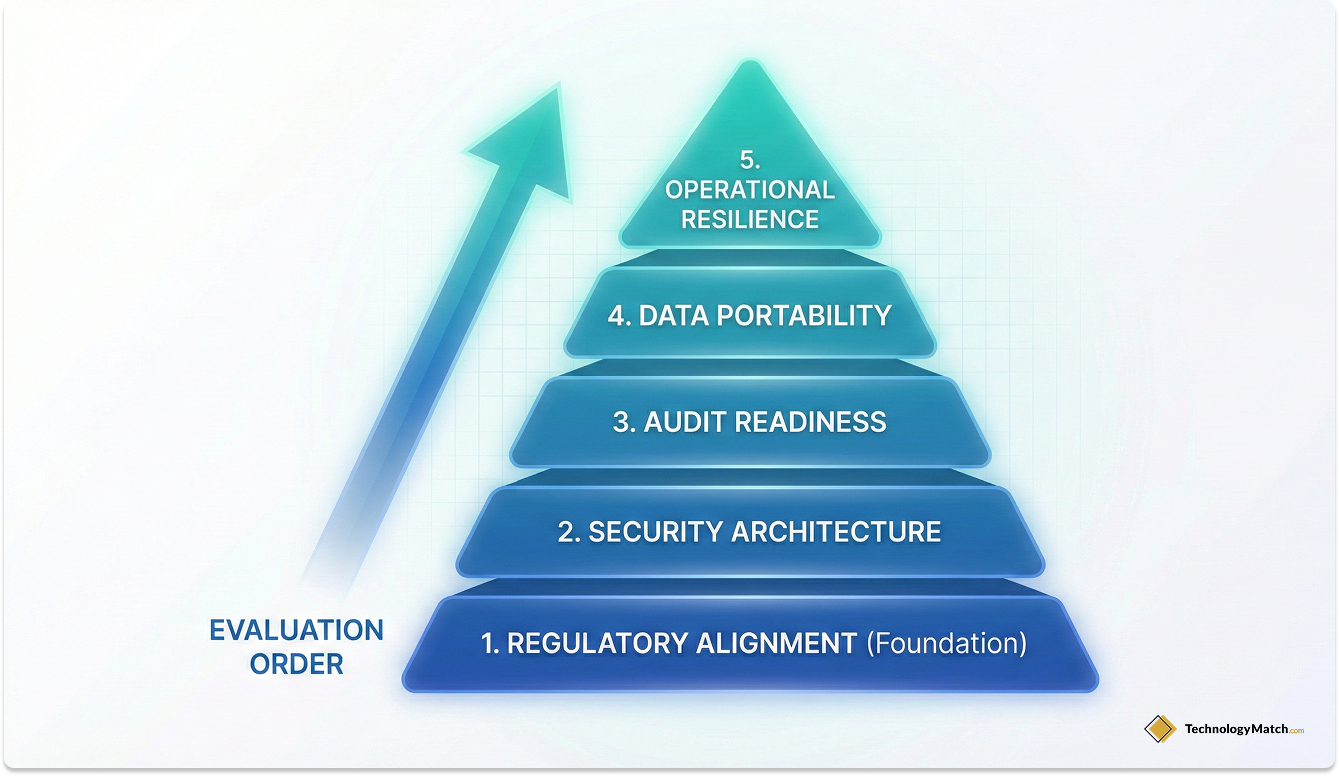
Layer 1: Regulatory Alignment (The Dealbreaker Layer)
Before you ever look at a user interface or discuss pricing, you must verify the vendor's alignment with your specific regulatory frameworks.
What to Evaluate:
- Does the vendor actively support the required compliance frameworks (SOC 2, HIPAA, ISO 27001, PCI-DSS)?
- Are their certifications current, and were they conducted by a reputable, independent third-party auditor?
The "Trust But Verify" Actions:
Do not accept a sales rep saying, "Yes, we are secure." Demand the documentation.
- Request the SOC 2 Type II report (not just the Type I, which only proves they designed a process, not that they actually follow it).
- Request the ISO 27001 certificate and the accompanying Statement of Applicability.
- For healthcare, ask for their standard BAA template upfront. If they say they need to use your BAA but require heavy redlining, factor that into your legal timelines.
Warning: A common mistake is assuming a vendor's overall compliance certification automatically covers the specific product module you are buying. Always verify the scope of the audit report.
Layer 2: Security Architecture Transparency
Once they prove regulatory alignment on paper, you must verify how that security is practically architected within the software. Compliance requires total visibility.
What to Evaluate:
- Encryption Standards: Are they using AES-256 for data at rest and TLS 1.2+ for data in transit? Do they support Bring Your Own Key (BYOK) so you maintain ultimate cryptographic control?
- Access Controls: Does the platform natively support SAML/SSO for integration with your Identity Provider (e.g., Entra ID, Okta)? Can you enforce Multi-Factor Authentication (MFA) and strict Role-Based Access Control (RBAC)?
- Vulnerability Management: Do they conduct regular third-party penetration tests?
The "Trust But Verify" Actions:
- Request their most recent Penetration Test Executive Summary. Look for how quickly they remediated critical findings.
- Ask for their Incident Response Plan and verify their contractual Service Level Agreements (SLAs) for breach notification.
Layer 3: Audit & Reporting Readiness
Compliance is not a state of being; it is the act of continuously proving you are doing the right thing. If an auditor walks into your office tomorrow, your vendor must be able to generate the necessary proof immediately.
What to Evaluate:
- Log Retention: How long does the vendor retain system, access, and change logs? Does it meet your regulatory minimums (e.g., 1 year, 7 years)?
- Log Immutability: Are the logs protected from tampering?
- SIEM Integration: Can the vendor automatically export these logs via API into your centralized Security Information and Event Management (SIEM) tool (like Splunk or Sentinel)?
The "Trust But Verify" Actions:
- Ask the vendor to demonstrate exactly how a compliance officer would pull an access report for a specific user over a 90-day period. If it requires a support ticket and a 48-hour wait, the vendor fails this layer.
Layer 4: Data Portability & Exit Strategy (Mitigating Lock-In Risk)
Vendor lock-in is frequently viewed as an operational or financial annoyance. In regulated industries, it is a severe compliance risk. If a vendor’s security posture degrades, or they fail an audit, you must be able to evacuate your data immediately.
What to Evaluate:
- Data Export Formats: Can you export your data in a standardized, usable format (CSV, JSON, SQL dump), or is it trapped in a proprietary format?
- Data Deletion: Does the vendor provide a cryptographically verified certificate of destruction when you terminate the contract?
- Sub-Processor Transparency: Who is the vendor relying on? Your risk extends to their hosting providers and support tools.
The "Trust But Verify" Actions:
- Ask: "What exactly happens to our data on Day 1 after our contract terminates?"
- Demand a complete list of their Fourth-Party Sub-Processors. If they refuse to disclose who hosts their underlying infrastructure, walk away.
Layer 5: Operational Resilience
Regulated industries cannot tolerate downtime. If a hospital's EHR goes down, patient care halts. If a trading platform drops, millions are lost. Operational stability is a compliance mandate.
What to Evaluate:
- Uptime SLAs: Are they offering 99.9% (approx. 8 hours of downtime a year) or 99.99% (approx. 52 minutes a year)?
- RPO and RTO: What is their Recovery Point Objective (how much data could be lost in a crash) and Recovery Time Objective (how fast will they be back online)?
- Redundancy: Is the architecture deployed across multiple availability zones or geographic regions?
The "Trust But Verify" Actions:
- Ask to see the results of their most recent Disaster Recovery (DR) test.
- Review the SLA contract language. Ensure the financial penalties for breaching the uptime guarantee are punitive enough to force the vendor to care.
The Compliance-Specific Vendor Evaluation Checklist
Do not reinvent the wheel for every procurement cycle. Standardize your intake process. Use this structured checklist to assess the primary components of vendor risk before you commit to technical evaluations.
Common Vendor Evaluation Mistakes in Regulated Industries
Even experienced IT directors make critical errors when evaluating software under pressure. Avoid these five common traps.
Mistake 1: Evaluating Features Before Compliance Fit
We have touched on this, but it bears repeating. In standard procurement, you might say, "Let's find the best tool for the job, and then we'll figure out how to secure it." In compliance-heavy industries, the security is the job. Evaluating features before verifying the SOC 2 report is a waste of engineering bandwidth. Compliance is binary.
Mistake 2: The Custom Security Questionnaire Bottleneck
Many enterprises attempt to manage risk by forcing vendors to fill out massive, 300-point custom Excel spreadsheets. This creates a massive bottleneck. Vendor security teams deprioritize custom spreadsheets, adding weeks to your procurement cycle. Then, your internal team has to spend days reading the subjective answers.
- The Fix: Stop sending custom spreadsheets. Require standard frameworks. Accept a current SOC 2 Type II report or a completed Cloud Security Alliance (CSA) CAIQ document. Standardized frameworks provide better, third-party-verified data in a fraction of the time.
Mistake 3: Ignoring Sub-Processor Risk (The Fourth-Party Problem)
You thoroughly audit the primary SaaS vendor, but you fail to ask who hosts their data. If your primary vendor passes their audit, but they use a cheap, non-compliant offshore hosting provider to store your data, you are exposed. Your compliance risk flows down the entire supply chain. You must review the vendor's vendors.
Mistake 4: Treating Certifications as Absolute Guarantees
A SOC 2 certification is not a magical shield. It simply means an auditor verified that the vendor follows the security policies they wrote for themselves. If they wrote weak policies, they can still pass a SOC 2 audit. You must read the actual report. Look closely at the "Exceptions" section to see where they failed controls during the testing period.
Mistake 5: Failing to Document an Exit Plan
Most organizations spend 95% of their energy on onboarding and 5% on offboarding. This creates data hostage situations. If you do not test the data export functionality during the evaluation phase, you will likely find out three years later that it is impossible to migrate your data out without paying exorbitant professional services fees.
When Internal IT Teams Lack Compliance Bandwidth
Conducting this level of rigorous due diligence requires immense internal bandwidth. It requires reading 80-page SOC 2 reports, cross-referencing sub-processor lists, and mapping features to regulatory controls.
Many regulated organizations are facing a reality of:
- Understaffed internal IT and security teams.
- Leadership transitions causing institutional knowledge gaps.
- Imminent audit deadlines creating artificial pressure.
- Exhausting M&A integrations that require rapid vendor consolidation.
In these situations, vendor evaluation often degrades from a strategic risk assessment into a rushed, reactive box-checking exercise. When your team is overwhelmed, they will inevitably skip the fine print in a vendor SLA or fail to review a critical Data Processing Addendum.
Vendor evaluation in regulated industries is not just procurement, it is risk containment. When you do not have the internal hours to run a 10-week, risk-first procurement cycle, you cannot simply skip the steps. You must change the methodology.
This is where outsourcing the "shadow work" of procurement becomes critical. By utilizing structured shortlisting and pre-vetted vendor pools, lean IT teams can drastically reduce their evaluation time, eliminate documentation friction, and effectively eliminate their exposure to non-compliant vendors before the process even begins.
Decision Tree: RFP vs. Pre-Vetted Shortlist
Should you run a traditional Request for Proposal (RFP), or should you leverage a technology matchmaker to deliver a pre-vetted shortlist? Use this logical framework to decide.
Run a Traditional RFP if:
- You have a dedicated, fully staffed internal procurement and compliance review team.
- Your project timeline is highly flexible (allowing for an 8 to 12-week cycle).
- You are mandated by strict government regulations to run a public, open bidding process for every purchase.
Use a Pre-Vetted Shortlist (Technology Matchmaker) if:
- Your internal IT and security teams are bandwidth-constrained and overwhelmed.
- You are facing an imminent compliance audit or renewal deadline and need to move fast.
- You cannot afford the risk of a vendor misstep or a failed implementation.
- You need to anonymously filter the market for vendors that already meet your strict SOC 2 or HIPAA baselines, saving you weeks of manual validation.

Time compression reduces compliance exposure. When you utilize a matchmaker acting as your "Employee No. 0," they take your Regulatory Dealbreaker Brief and filter the market for you. You only spend your valuable time evaluating the three vendors who have already proven they can pass your security audits.
Integrating Compliance Into Your Scoring Model
When you finally bring your pre-vetted shortlist to the decision table, your weighted scoring matrix must reflect the realities of your industry. Do not weight "User Interface" equally with "Audit Readiness."
Here is a baseline weighted scoring model optimized for highly regulated environments:
By forcing the scoring model to heavily favor risk containment (85% of the total score), you mathematically prevent your organization from buying a "pretty" tool that will fail your next compliance audit.
Looking for IT partners?
Find your next IT partner on a curated marketplace of vetted vendors and save weeks of research. Your info stays anonymous until you choose to talk to them so you can avoid cold outreach. Always free to you.
FAQ
How do you evaluate IT vendors for SOC 2 compliance?
Do not just ask if they are compliant. Request their current SOC 2 Type II report. Review the auditor's opinion, carefully examine the scope of the systems covered, verify the testing period (it should be within the last 12 months), and critically assess any noted exceptions or failures in their controls.
What should be included in a HIPAA vendor checklist?
A HIPAA vendor evaluation must include their willingness to sign your Business Associate Agreement (BAA) without heavy redlining. It must also verify AES-256 encryption at rest, TLS 1.2+ in transit, granular access controls, and strict, contractually guaranteed breach notification timelines.
How do you reduce vendor risk in regulated industries?
You reduce risk by adopting a Risk-First Evaluation Framework. Disqualify vendors immediately if they cannot provide third-party validated compliance documentation. Furthermore, replace custom 100-page security questionnaires with standardized frameworks (like SIG or CAIQ) to get accurate security data faster, and utilize pre-vetted shortlists to avoid the noise of non-compliant vendors.
What documents should vendors provide during a compliance review?
At a minimum, demand their SOC 2 Type II report, ISO 27001 certificate (if applicable), a recent Penetration Test Executive Summary, a complete Sub-processor Disclosure list, their Data Processing Addendum (DPA), and their documented Disaster Recovery SLAs.
How do you avoid vendor lock-in in healthcare IT?
Address the exit strategy before you sign the contract. Ensure the vendor allows for bulk data exports in standardized, non-proprietary formats. Verify their contractual data deletion processes (getting a certificate of destruction), and negotiate egress fees upfront so you aren't penalized financially for leaving.